What Is the Certified Information Systems Security Professional Certification?

Becoming a Certified Information Systems Security Professional (CISSP) gives you a globally recognized qualification in the information security field. You can earn the certification, offered by ISC2, by demonstrating your expertise across eight domains.
The benefits of earning the CISSP certification include better job opportunities, higher salaries, and credibility. You will also have access to a network of leaders in the field. Furthermore, organizations benefit when they can hire people with proven knowledge and skills as well as a shared approach and commitment to cybersecurity best practices.
What Are the Prerequisites for CISSP Certification?
You cannot earn this certification simply by studying and taking a test. The credential has experience requirements and stipulates other essentials. You will need at least five cumulative years of industry experience, including full-time work in two or more of the eight exam domains, though internships and part-time work may also be applied. You may be able to count other achievements toward that requirement, as well, such as:
- A bachelor’s or master’s in computer science, information technology, or cybersecurity, which may count toward up to a year of the experience requirement
- A credential on the list approved by ISC2, which may also count toward up to a year
What Are the 8 Domains on the CISSP Exam?
Earning your CISSP requires that you have expertise across eight areas to design, implement, and then manage a comprehensive cybersecurity program.
Cybersecurity is multidisciplinary, having technical and managerial aspects that fit together to protect systems and data. That’s why the exam requires well-rounded expertise across the eight domains. Being a specialist in one area is not effective against the broad and sophisticated threat actors of today.
The following overview of CISSP domains gives you an idea of the breadth and depth of knowledge required.
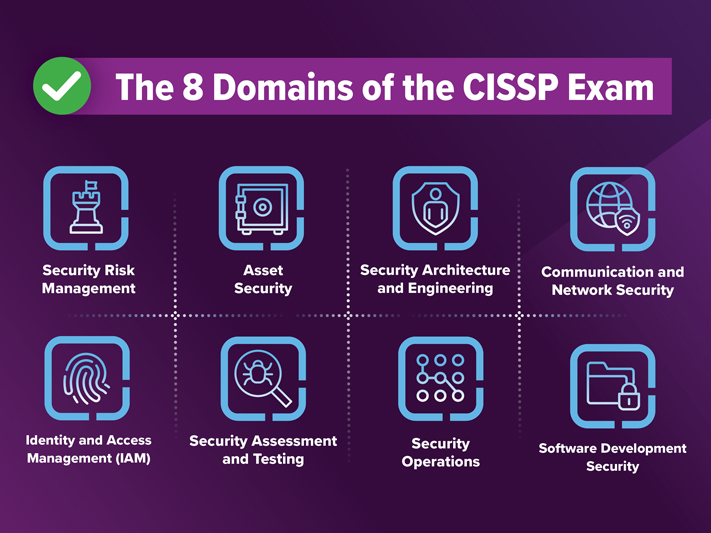
Security Risk Management
This domain encompasses the foundational principles, policies, approaches to risk assessment, and cybersecurity frameworks for governance, compliance, and ethical practices that underpin effective cybersecurity. They are based on the initialism “CIA” for confidentiality, integrity, and availability of your IT systems and data.
Asset Security
Your data, applications, and infrastructure are key digital operational assets that need protection. This domain is about classifying the assets, determining ownership, and ensuring the proper handling of data from its creation to eventual archiving or destruction. In short, it’s about defining who can access what and under what conditions.
Security Architecture and Engineering
Security needs to be designed into systems and technologies from the beginning. Cybersecurity techniques around cryptography, as well as both hardware and software architecture, must be considered at every step.
Communication and Network Security
In our connected world and with so much computing done in the cloud, the secure design and protection of networks is paramount. Defending data in motion requires firewalls, VPNs, network protocols, and communication channels that are kept secure.
Identity and Access Management (IAM)
Controlling access and managing the identity of systems and data users keeps threat actors out. This CISSP domain covers authentication, authorization, conditions of access, and levels of access. Recordkeeping and compliance are also vital in this area.
Security Assessment and Testing
Cybersecurity is a dynamic concept that constantly changes based on threats, techniques, and trends. This domain is about constantly checking and testing the effectiveness of your cybersecurity programs. It covers tools and techniques, how to conduct audits and penetration tests, and how to assess and respond to vulnerabilities.
Security Operations
This domain is composed of the everyday operations and tasks of running a cybersecurity program, including responding to incidents. Logging, monitoring, recordkeeping, and reporting play a part, as does responding to attacks, mitigating damage, and recovering to keep systems operating.
Software Development Security
Security that’s designed into all phases of software development is a must. Secure development practices, including secure coding, testing, and documentation, are part of software life cycle management.
Prepare for the CISSP Exam with Excelsior
Excelsior University’s Bachelor of Science in Cybersecurity program not only is academically rigorous, including hands-on experience, but also prepares you for the CISSP exam. What’s more, a bachelor’s degree in a relevant field could lower your experience requirement by up to a year. But earning your Excelsior degree prepares you for so much more than just a certification; you’ll be picking up the hard and soft skills necessary to build a successful career. And if you seek leadership positions within the field, you can transition seamlessly into Excelsior’s MS in Cybersecurity program.
Earning a degree from Excelsior opens the door to a wide array of job opportunities in the field of cybersecurity. And adding the CISSP credential takes you to another level. Contact Admissions when you’re ready to take the first step toward your dream career.



